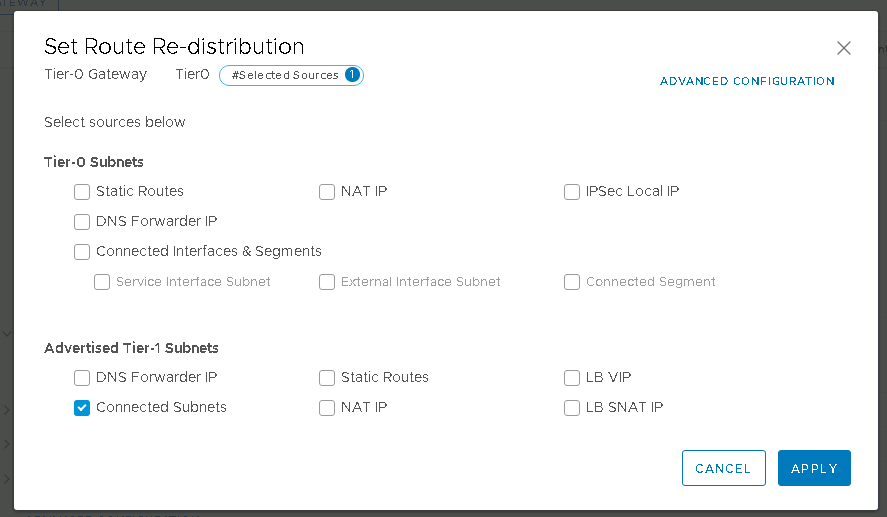
Very useful commands for juniper EX switches
How to configure Interfaces, OSPF, Voip, LLDP, QOS, Access lists, Routes
and more
General commands
show mac-address table
show ethernet-switching table brief
show switches that directly conected
show lldp neighbors
config vlan
set vlans Floor_Users vlan-id 90
set vlans Floor_Users l3-interface vlan.90
set interfaces vlan unit 90 family inet address 10.10.10.254/24
assign vlan to port
set interfaces unit 0 family ethernet-switching vlan members
upgrade (mybe needed – set system services ftp, when upgrading 8200 need to upgrage both Route Engines)
request system software add ftp://a:123456@10.10.10.81/jinstall-ex-3200-9.6R1.13-domestic-signed.tgz
enable SSH
set system services ssh
show ip addresses
show interfaces terse
show all ports info
show interfaces extensive
load factory-default
load factory-default
show rollback 10
file show /var/db/config/juniper.conf.10.gz
show int statistics at real time
run monitor interface ge-0/0/0
like tcpdump
run monitor traffic interface ge-0/0/0
to add config from notepad
load update terminal
static route
set routing-options static route 192.168.16/24 next-hop 1.1.1.1
start terminal monitor
monitor start /var/log/messages
stop terminal monitor
monitor stop
check what is going to be commited
show | compare
time
show system uptime
show modules / hardware
show chassis hardware
Show ospf interfaces
show ospf interface
ospf – redis static
set protocols ospf export redistribute-into-OSPF
set policy-options policy-statement redistribute-into-OSPF term static from protocol static
set policy-options policy-statement redistribute-into-OSPF term static then accept?
LACP -switches
set chassis aggregated-devices ethernet device-count 5
set interfaces ae0 aggregated-ether-options lacp active
set interfaces ge-0/0/0 ether-options 802.3ad ae0
set interfaces ge-0/0/1 ether-options 802.3ad ae0
set interfaces ae0 unit 0 family inet address 10.10.0.254/24
LACP – J routers
set chassis aggregated-devices ethernet device-count 5
set interfaces ae0 aggregated-ether-options lacp active
set interfaces ge-0/0/0 gigether-options 802.3ad ae0
set interfaces ge-0/0/1 gigether-options 802.3ad ae0
set interfaces ae0 unit 0 family inet address 10.10.0.254/24
password recovery
* reload the switch
* stop the boot by presing the "space bar"
* choose 'recovery'
boot -s
NTP
set system ntp server 1.1.1.1
exit
set date ntp
create rescue config
request system configuration rescue save
set managment ip at stack
set interfaces vme unit 0 family inet address 10.10.10.235/24
connect to a specific switch from a stack
request session member
install image from USB
1. Put the new code(desired version of JUNOS) on a USB which is formatted under FAT32 and insert on the back of the switch where you can find the USB slot.
2. Reboot the device and when it says loading press spacebar to take us to loader prompt (loader>).
3. Type the following command to reinstall junos from this prompt
loader>install --format file:///filename.tgz
* where filename is like eg: jinstall-ex-9.2R1.5-domestic-signed.tgz
copy log files from specific unit
request session member 5
start shell user root
! -Password-
tar -zcvf varlog-mem5.tar.gz /var/log/
mv varlog-mem5.tar.gz /var/tmp/
exit
file copy fpc5:/var/tmp/varlog-mem5.tar.gz fpc0:/var/tmp
! Then open with web - Maintain --> Files --> temp
show alarms
(use to check why the alarm led is red)-
show system alarms
vrrp
set interfaces vlan unit family inet address x.x.x.x /24 vrrp-group virtual-address x.x.x.x priority < priority>
vrrp – backup master (Specify that the backup router can process packets with an IP destination address of the virtual address)
ip vrrp 22 accept-data
ECMP
(equal cost multi path)
set policy-options policy-statement load-balancing-policy then load-balance per-packet
set routing-options forwarding-table export load-balancing-policy
allow NSM to connect to the switch
set system services netconf ssh
dhcp snooping
set ethernet-switching-options secure-access-port vlan all examine-dhcp
bpdu guard
set protocols rstp bpdu-block-on-edge
set protocols rstp interface all edge
port mirroring
set ethernet-switching analyzer analyzer1 input ingress interface ge-0/0/0
set ethernet-switching analyzer analyzer1 input egress interface ge-0/0/0
set ethernet-switching analyzer analyzer1 output interface ge-0/0/2
LLDP – MED
(the switch tells the ip phone what is the voice vlan)
set vlans description voice-vlan
set vlans interface ge-0/0/2.0
set interfaces unit 0 family ethernet-switching vlan members
set interfaces unit 0 family ethernet-switching port-mode access
set ethernet-switching-options voip interface .0 vlan
set ethernet-switching-options voip interface .0 forwarding-class assured-forwarding
set protocols lldp-med interface
tacacs
(use “load merge terminal” to load this format of config)
system {
time-zone Asia/Jerusalem;
authentication-order tacplus;
root-authentication{
encrypted-password "$1$gzwtefgipDYmub7XcCTEU4/"; ## SECRET-DATA
}
tacplus-server {
secret "$9$y45645XxjqfT9CRhSyMX-dsYgJ";
secret "$9$vD4574745dV.5Fnu0ylKvxdsYoaZj";
}
accounting {
events [ login change-log interactive-commands ];
destination {
tacplus;
}
}
}
Voip QOS marking
class-of-service{
classifiers {
dscp juniper_dscp_classifier {
import default;
forwarding-class voice {
loss-priority low code-points 101110;
}
}
ieee-802.1 juniper_ieee_classifier {
import default;
forwarding-class voice {
loss-priority low code-points 011;
}
}
}
forwarding-classes {
class voice queue-num 7;
class expedited-forwarding queue-num 5;
class assured-forwarding queue-num 1;
class best-effort queue-num 0;
}
interfaces {
vlan {
unit 12 {
classifiers {
dscp juniper_dscp_classifier;
}
}
}
}
}
access-lists of ip addresses that allowd to access the switch (use “load merge terminal” to load that format of config)
interfaces{
lo0 {
unit 0 {
family inet {
filter {
input Telnet-access-filter;
}
}
}
}
}
firewall {
family inet {
filter Telnet-access-filter {
term team_X {
from {
source-address {
x.x.x.x/32;
x.x.x.x/32;
}
protocol tcp;
}
then accept;
}
term team_Y {
from {
source-address {
y.y.y.y/32;
y.y.y.y/32;
}
protocol tcp;
}
then accept;
}
term Access_from_forbidden_addresses {
from {
source-address {
127.0.0.0/8;
}
protocol tcp;
}
then discard;
}
term OSPF {
from {
protocol ospf;
}
then accept;
}
term icmp {
from {
protocol icmp;
}
then accept;
}
term accept_DHCP {
from {
protocol udp;
}
then accept;
}
}
}
}
4200 EX Switches
set that if disconnecting cascade cables from stack of 2 switches that the switches will not became layer 2
set virtual-chassis no-split-detection
show units at stack
show virtual-chassis
0 (FPC 0) Prsnt BQ0209341890 ex4200-48p 128 Master* 1 vcp-0
1 (FPC 1) Prsnt BN0209364440 ex4200-24p 128 Linecard 3 vcp-0
2 (FPC 2) Prsnt BQ0209341900 ex4200-48p 128 Backup 0 vcp-0
3 (FPC 3) Prsnt BQ0209341917 ex4200-48p 128 Linecard 2 vcp-0
Member ID for next new member: 4 (FPC 4)
change units number
(the serial is also at the back of the switch, no restart needed, the new master became master after few minutes)
set virtual-chassis preprovisioned
set virtual-chassis member 0 serial-number BN0209364440 role routing-engine
set virtual-chassis member 1 serial-number BQ0209341917 role routing-engine
set virtual-chassis member 2 serial-number BQ0209341900
set virtual-chassis member 3 serial-number BQ0209341890
8200 EX Switches
set managment ip when having 2 routing engines
delete int me0
edit groups
set re0 system host-name Name1
set re0 interfaces me0 unit 0 family inet address 10.10.10.12/24
set re1 system host-name Name2
set re1 interfaces me0 unit 0 family inet address 10.10.10.22/24
top
set apply-groups [re0 re1]
turn off a module
(disable)
set chassis fpc power off
set the switchover without only 10 packet loss
set chassis redundancy graceful-switchover
connect to backup routing engine
request routing-engine login backup
show modules
show chassis hardware
change active CPU
request chassis routing-engine master switch
cancel switchover at fuiler/reload command
deactivate chassis redundancy graceful-switchover
Auto save config aldo to backup
(“commit” saves only to the present Routing Engine)
commit synchronize
Run commands at a linecard
root@st-grande06-scb0:RE:0% lcdd 2 chassism
chassism#show mac ge-2/0/1
chassism#show phy ge-2/0/1
The post ![sharon saadon]() Juniper EX switches configuration examples appeared first on SharonTools.
Juniper EX switches configuration examples appeared first on SharonTools.
 NX-OS general commands appeared first on SharonTools.
NX-OS general commands appeared first on SharonTools.